Our Approach to MAS TRM Compliance Audit
Requirement Analysis
Defining The Scope
In-Depth Gap Analysis
Awareness Session
Asset Inventory
Risk Assessment
Risk Treatment
SOP Document Set
Security Assessments
Mitigation Consulting
End User Training
Final Gap Analysis
What is a MAS TRM Compliance Audit?
A MAS TRM Compliance Audit is an independent assessment of a financial institution’s (FI) compliance with the Technology Risk Management (TRM) guidelines issued by the Monetary Authority of Singapore (MAS). The audit is conducted to ensure that the FI has implemented appropriate controls to manage its technology risks and maintain IT and cyber resilience.
In short, it is an audit to ensure that financial institutions in Singapore are following the MAS’s guidelines on technology risk management.
Deliverables of Compliance Audit & Certification
- Executive Presentation: provide high level executive summaries of the complete engagement, root cause analysis of the identified issues & best practice recommendations for the long-term to help leaders better understand their risk and incorporate our recommendations into their roadmap.
- Detailed Audit Reports: The audit report will typically be a detailed document that is divided into several sections, including:
- Introduction: This section will provide an overview of the audit, including the scope, objectives, and methodology.
- Findings: This section will identify the areas of compliance and non-compliance.
- Recommendations: This section will make recommendations for improvement.
- Appendices: This section may include supporting documentation, such as interview transcripts, policies and procedures, and risk assessments.
- Certificate of Compliance: The certificate of compliance is a formal document that is issued by the auditor to the organization. This document states that the organization has been found to be in compliance with the guidelines.
- List of Recommendations for Improvement: The list of recommendations for improvement will identify areas where the organization can strengthen its technology risk management framework. These recommendations can be used by the organization to improve its security posture and reduce its risk of a data breach or other security incident.
- Plan for Remediation: The plan for remediation will outline the steps that the organization will take to address any non-compliance findings. This plan should be specific and measurable, and it should include a timeline for completion.
Benefits of a MAS TRM Compliance Audit
Increased customer confidence
A MAS TRM Compliance Audit demonstrates to customers that your organization is committed to protecting their financial information.
Reduced risk of fines and penalties
Failing to comply with MAS TRM requirements can result in significant fines and penalties. An audit can help you identify and mitigate risks so you can avoid these consequences.
Enhanced reputation
Achieving MAS TRM compliance demonstrates to stakeholders that your organization is a responsible and ethical actor. This can enhance your reputation and attract new customers and partners.
Improved operational efficiency
A MAS TRM Compliance Audit can help you identify and implement improvements to your financial crime controls, which can lead to improved operational efficiency.
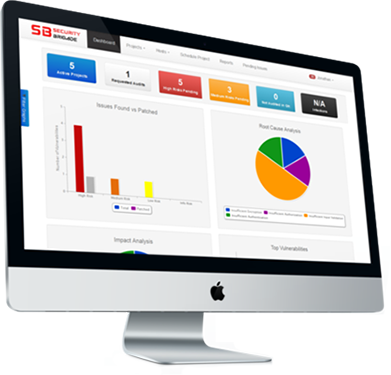
Real-Time Customer Dashboard
Our Real-Time Customer Dashboard delivers transparency during our assessments and provides customers with a dynamic view of our security assessment and compliance services.
The dashboard enables customers to track all their projects through a single platform, manage timelines, track open issues, allocate responsibilities internally, learn about remediating issues etc. It also allows customers to get a real-time view into individual projects as they are being executed, track requirements, learn about identified issues, resolve tickets etc.
The dashboard allows for seamless collaboration between customer & our teams to ensure that we execute and deliver the absolute best and most comprehensive assessments.