The VSCC Certificate (SBI) – Vendor Site Compliance Certificate is a compliance mandate given by SBI to ensure appropriate security best practices and controls deployed on merchant websites that are integrated with their payment gateways
As per the details shared by SBI, the Vendor Site Compliance Certificate (VSCC) can only be issued by CERT-In Empanelled Auditor and is only required for private merchants. Government clients and reputed educational institutes can self certify the Form C.
Key Criteria for VSCC Certificate – Vendor Site Compliance Certificate
Based on the Vendor Site Compliance Certificate (VSCC Form C) questionnaire, the following key criteria need to be covered as part of this audit.
- SSL Certificate & Encryption
- Web-Application Penetration Testing
- Network Vulnerability Assessment
- Network Penetration Testing
- Firewall
- System Audit Report for Data Storage & Localization
- Audit Trail & Logging
- PCI DSS (if applicable)
- Data Sharing & Privacy
The VSCC Form C must filled, signed & certified by a CERT-IN empanelled auditor which can then be submitted to SBI as part of the merchant on-boarding process.
Sample Checklists & Questionnaires
Approach for VSCC Certificate – Vendor Site Compliance Certificate
Based on our extensive experience with VSCC Certificate (SBI) – Vendor Site Compliance Certificate, we have developed the following approach:
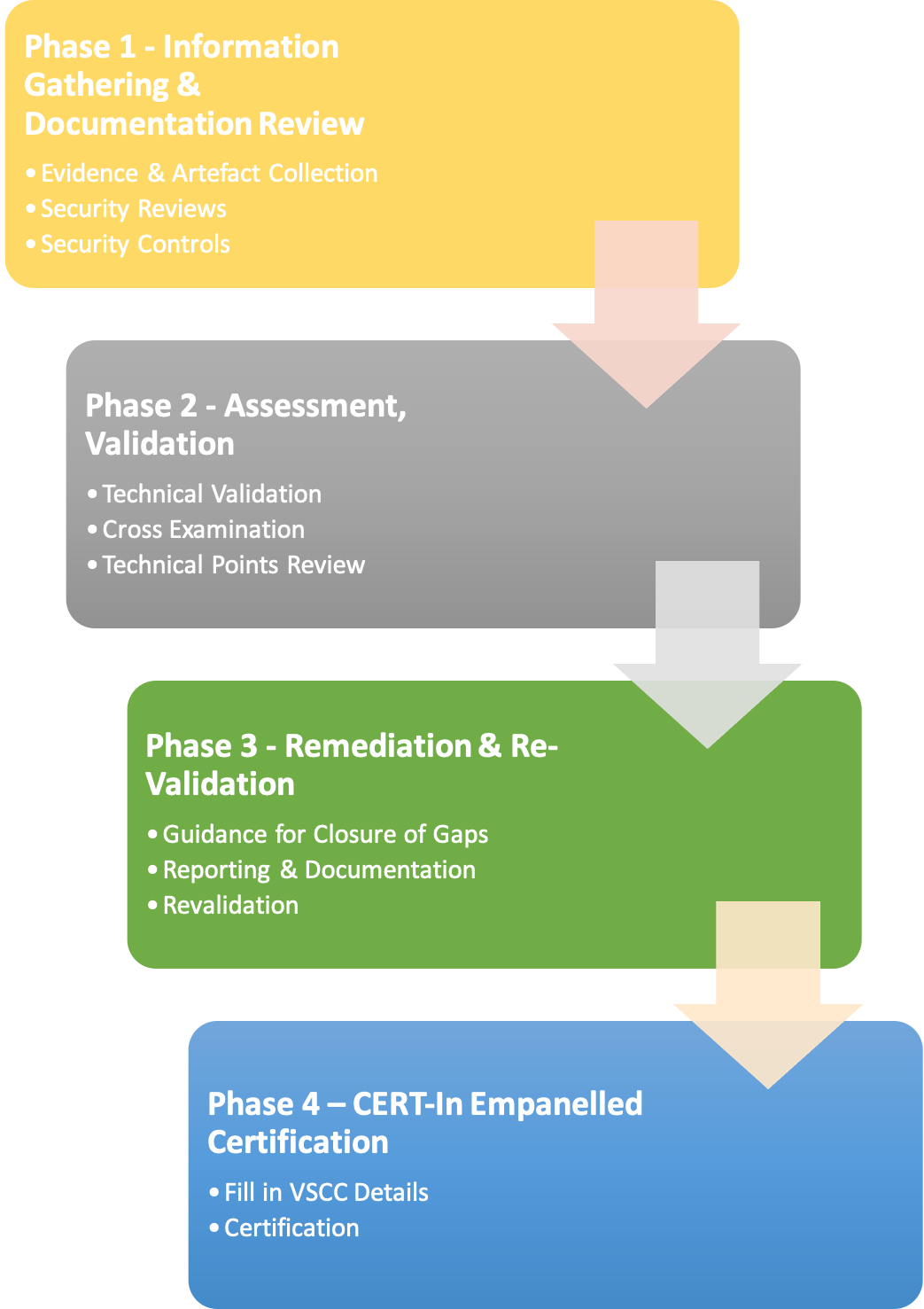
Phase 1 – Information Gathering & Documentation Review
A detailed questionnaire is shared with your teams and various documentation and evidences are collected on existing security reviews & controls in place. These documents are thoroughly reviewed by our experts to understand the implementation and flag any concerns.
Phase 2 – Assessment & Validation
As part of this phase, an analysis of is carried out to validate all the documentation and cross-examine artefacts provided. Along with this the technical points are assessed in-line with best-practices and the VSCC Questionnaire requirements.
Phase 3 – Remediation & Re-Validation
A comprehensive report is provided with any areas of concern, risks or violations. Appropriate recommendations are provided along with detailed proof of concept details to help your teams understand the concerns raised.
Our team works with you to carry out re-validation to ensure that you are able to close all the gaps and achieve successful compliance.
Phase 4 – CERT-In Empanelled Certification
As a CERT-In Empanelled Auditor, we capture the entire activity along with relevant documentation, artefacts, findings, recommendations etc. The Vendor Site Compliance Certificate (VSCC) is filled in with the relevant details and as authorised CERT-In Empanelled Auditors, this form is then signed, sealed and delivered to the customer.
Deliverables of Compliance Audit & Certification
- Executive Presentation: provide high level executive summaries of the complete engagement, root cause analysis of the identified issues & best practice recommendations for the long-term to help leaders better understand their risk and incorporate our recommendations into their roadmap.
- Detailed Audit Reports: The audit report will typically be a detailed document that is divided into several sections, including:
- Introduction: This section will provide an overview of the audit, including the scope, objectives, and methodology.
- Findings: This section will identify the areas of compliance and non-compliance.
- Recommendations: This section will make recommendations for improvement.
- Appendices: This section may include supporting documentation, such as interview transcripts, policies and procedures, and risk assessments.
- Certificate of Compliance: The certificate of compliance is a formal document that is issued by the auditor to the organization. This document states that the organization has been found to be in compliance with the guidelines.
- List of Recommendations for Improvement: The list of recommendations for improvement will identify areas where the organization can strengthen its technology risk management framework. These recommendations can be used by the organization to improve its security posture and reduce its risk of a data breach or other security incident.
- Plan for Remediation: The plan for remediation will outline the steps that the organization will take to address any non-compliance findings. This plan should be specific and measurable, and it should include a timeline for completion.