Network Vulnerability Assessment is a process we use to identify, classify, and prioritize vulnerabilities in your network systems. Think of it as a health check-up for your network, uncovering any weaknesses that could be exploited by cyber threats.
We focus on various vulnerabilities, including software flaws, outdated systems, and configuration errors. Our goal is to ensure every nook and cranny of your network is scrutinized for potential risks.
What is a Network Vulnerability Assessment (VA)?
A network vulnerability assessment is a security assessment that identifies and prioritizes vulnerabilities in a network. It is a critical part of any organization’s cybersecurity program, as it can help to identify and fix security weaknesses before they can be exploited by attackers.
The results of a network vulnerability assessment are typically presented in a report that lists the identified vulnerabilities, their severity, and recommendations for remediation.
Network vulnerability assessments should be conducted on a regular basis, such as annually or quarterly. This will help to ensure that the organization’s security posture is continuously improving.
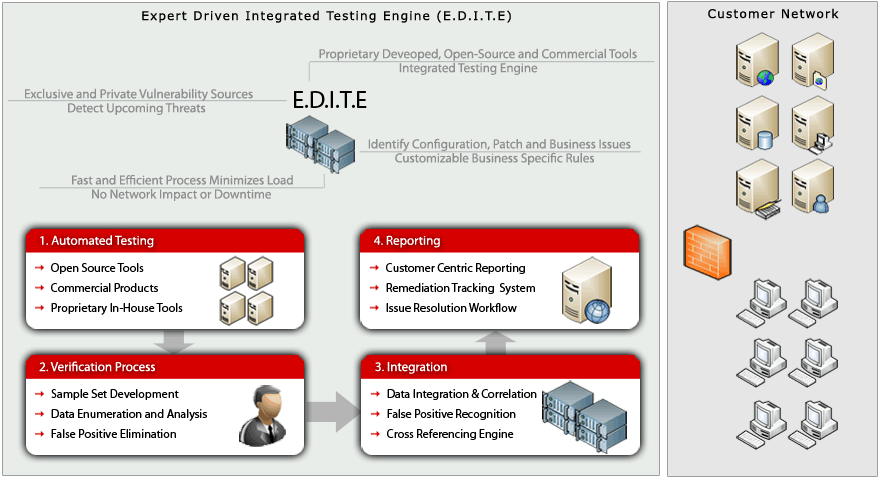
Our Approach to Network Vulnerability Assessment (VA)
Our approach to Network Vulnerability Assessment is thorough and adaptive. Combining our expert team of security analysts with cutting edge and industry leading Vulnerability Scanners, we can deliver an optimal experience for our customers. The key steps in our process are:
Vulnerability Assessment vs Penetration Testing
Vulnerability Assessment and Penetration Testing are essential, yet distinct components of a comprehensive cybersecurity strategy. Vulnerability Assessment is a broad and regular process of identifying and prioritizing potential weaknesses in a system, providing a comprehensive overview of security vulnerabilities. In contrast, Penetration Testing is a targeted, attack-simulating exercise designed to exploit these vulnerabilities, offering a real-world perspective on the effectiveness of existing security measures. While they differ in approach and focus, together they provide a holistic view of an organization’s security posture.
Regular vulnerability assessments combined with periodic penetration tests ensure a robust defense against evolving cyber threats, making them indispensable for organizations aiming to safeguard their digital assets.
Learn More about Vulnerability Assessment vs Penetration Testing.
Deliverable of Our Network Vulnerability Assessment (VA)?
- Executive Presentation: provide high level executive summaries of the engagement, key root cause analysis of the identified issues & best practice recommendations for the long-term to help leaders better understand their risk and incorporate our recommendations into their roadmap.
- Detailed Technical Reports: provide in-depth descriptions, step by step proof of concepts, detailed recommendations with source-code & configuration examples of all the security issues identified as part of the assessment. Security issues identified are risk-rated based on the Common Vulnerability Scoring System (CVSS) and mapped to industry leading standards such as OWASP Web Top 10, OWASP Mobile Top 10, etc.
- Safe To Host Security Certificate: The certificate of compliance is a formal document that is issued by the auditor to the organization. This document states that the organization has been found to be in compliance with the guidelines.
- List of Recommendations for Improvement: The list of recommendations for improvement will identify areas where the organization can strengthen its technology risk management framework. These recommendations can be used by the organization to improve its security posture and reduce its risk of a data breach or other security incident.