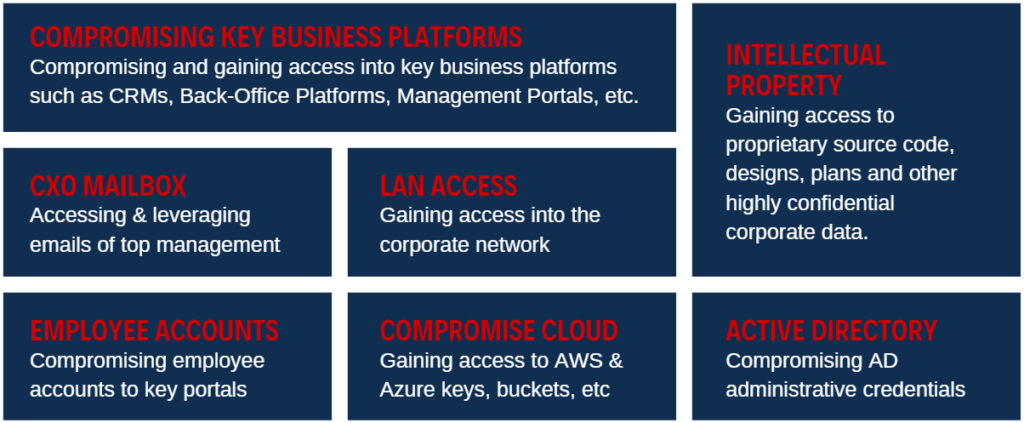
Red Team Assessments are the pinnacle of security testing, simulating the tactics and persistence of real-world attackers. Unlike traditional network penetration testing, which focuses on finding as many vulnerabilities as possible, Red Team Assessments aim to test your organization’s detection and response capabilities in a holistic manner. This approach not only uncovers weaknesses but also tests the effectiveness of your security measures under real attack scenarios.
What is a Red Team Assessment?
The Red Team Assessment engagement consists of a realistic, “no-holds-barred” attack scenario in your environment. The Security Brigade red team uses any non-destructive methods necessary to accomplish a set of jointly agreed upon mission objectives while simulating attacker behaviour.
The red team closely mimics a real attacker’s active and stealthy attack methods by using tactics, techniques and procedures seen on real, recent incident response engagements. This helps assess your security team’s ability to detect and respond to an active attacker scenario.
Our Approach to Red Team Assessment
At Security Brigade, our Red Team Assessments are not just a service; they are a comprehensive, state-of-the-art experience in simulating and defending against sophisticated cyber threats. Our unique approach incorporates a blend of advanced technologies and innovative strategies to provide an unparalleled assessment of your security posture.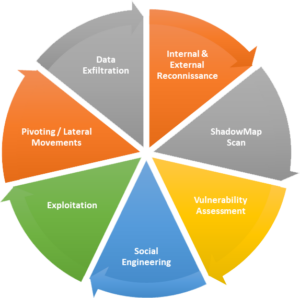
Our Red Teams utilize ShadowMap, our cutting-edge Attack Surface Management Platform, to gain a comprehensive view of your organization’s digital footprint. ShadowMap is engineered to uncover and map out every aspect of your digital presence, just as an actual attacker would. This platform forms the backbone of our assessment strategy, enabling us to identify and exploit vulnerabilities that might otherwise go unnoticed.
Through our Digital Risk Management Platform, we simulate these tactics by leveraging platforms and resources that real-world hackers commonly use. This includes Dark Web Credentials, Code Leaks on GitHub & Bitbucket, Exposed APIs and Tokens, Leaked Files etc.
Types of Red Teams – Red, Blue or Purple?
Red Teams: are the attackers that are playing the role of the motivated external attacker that is targeting your organization. They are designed to test the effectiveness of an organization’s defenses by emulating its adversaries TTPs in a continuous and evolving manner.
Blue Team: are the internal or partner teams responsible for building security controls, detection and response. Our team may join your Blue Team to supplement their capabilities & leverage our vast experience dealing with incidents. Blue Teams are designed to keep the organization safe from real-world attackers by understanding their TTPs and evolving the company’s defenses.
Purple Team: is a single team of consultants that are the middle-ground between the red & blue teams. They are designed to enhance information sharing between the Red and Blue teams to maximize their respective and combined effectiveness.
Learn More about the Types of Red Team Assessments
Using Attack Surface Management in Red-Team Assessment
ShadowMap is our award winning Attack Surface & Digital Risk Management platform & the latest innovation from the Security Brigade R&D team.
We leverage our ShadowMap platform to generate a complete picture of your global technology exposures and its associated risks. This data is cross-referenced with our Active + Passive Threat Intelligence modules to identify key risks and misconfigurations.
The ShadowMap Scan report allows our red-team to get a rapid picture of your complete technology footprint, allowing them to quickly identify easy access points into your infrastructure that can be leveraged as part of the red-team assessment.
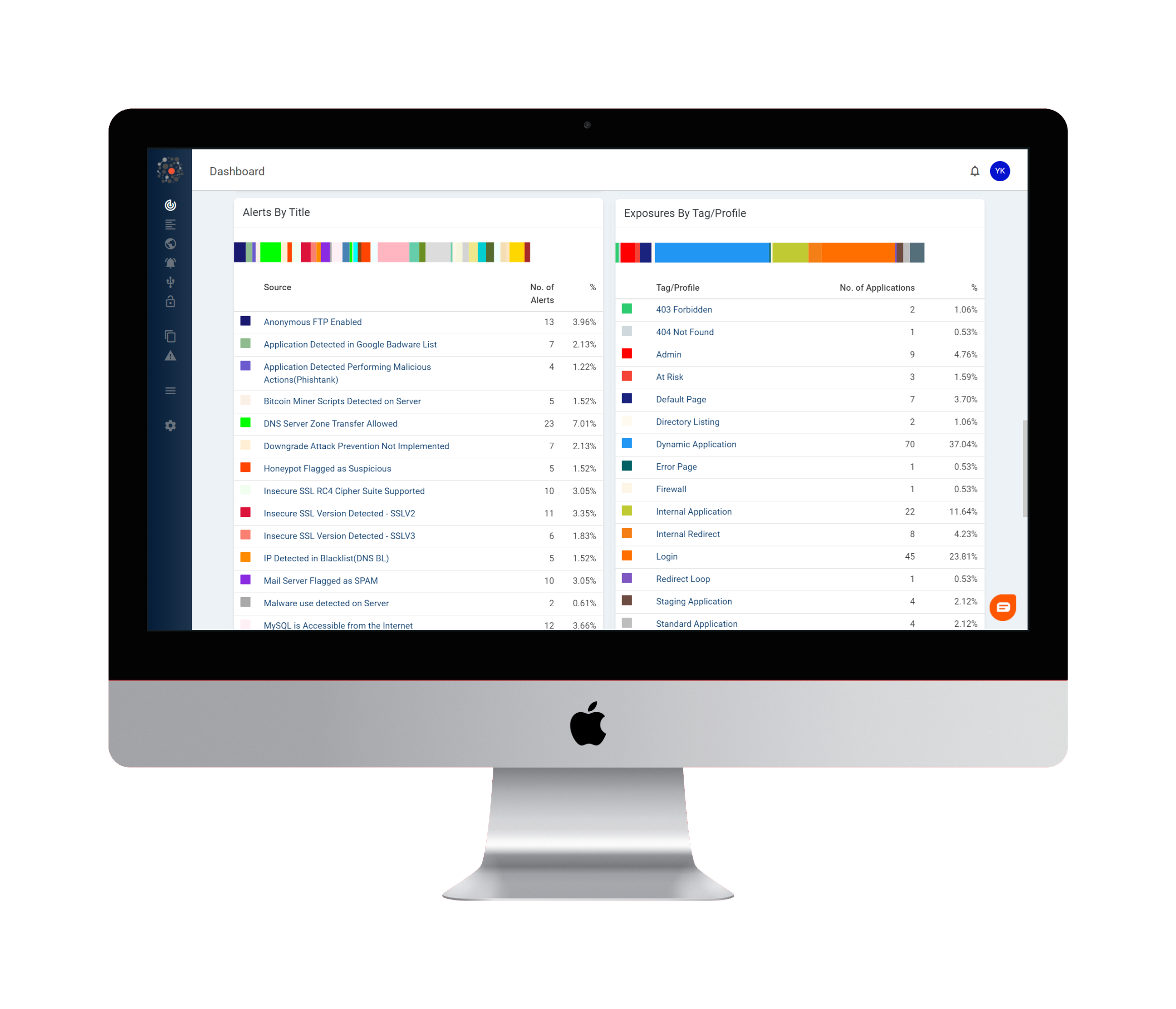
Deliverable of Our Red Team Assessment?
- Executive Presentation: provide high level executive summaries of the engagement, key root cause analysis of the identified issues & best practice recommendations for the long-term to help leaders better understand their risk and incorporate our recommendations into their roadmap.
- Detailed Technical Reports: provide in-depth descriptions, step by step proof of concepts, detailed recommendations with source-code & configuration examples of all the security issues identified as part of the assessment. Security issues identified are risk-rated based on the Common Vulnerability Scoring System (CVSS) and mapped to industry leading standards such as OWASP Web Top 10, OWASP Mobile Top 10, etc.
- Safe To Host Security Certificate: The certificate of compliance is a formal document that is issued by the auditor to the organization. This document states that the organization has been found to be in compliance with the guidelines.
- List of Recommendations for Improvement: The list of recommendations for improvement will identify areas where the organization can strengthen its technology risk management framework. These recommendations can be used by the organization to improve its security posture and reduce its risk of a data breach or other security incident.