There are several different Types of Security Audits that are intended to meet the business requirements of different companies and market segments. Each approach has its own benefits and drawbacks and the right approach for any particular organization depends on their objective for carrying out the audit along with their key concerns and risk areas.
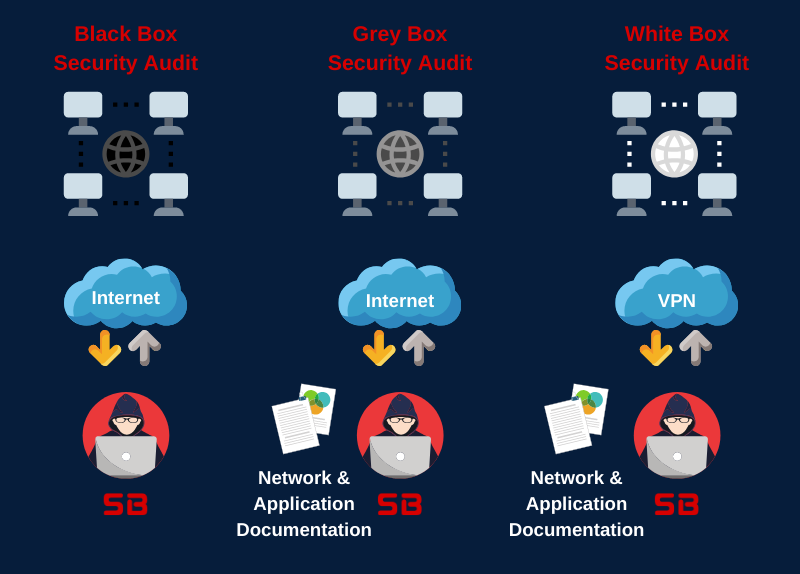
There are three main types of security assessments: white box, grey box, and black box.
- White box: In a white box assessment, the tester has full knowledge of the system or network being tested, including the source code, network diagrams, and configuration files. This allows the tester to perform a more comprehensive assessment, as they can understand how the system works and how vulnerabilities could be exploited.
- Grey box: In a grey box assessment, the tester has some knowledge of the system or network being tested, but not as much as in a white box assessment. This might include information such as the network architecture, the operating system, and the web application framework.
- Black box: In a black box assessment, the tester has no knowledge of the system or network being tested. This means that the tester must rely on their own skills and knowledge to identify vulnerabilities.
What Types of Security Audit is right for my organization?
The best type of security assessment for you will depend on your specific needs and goals. If you are concerned about a particular vulnerability, such as a known security flaw in a piece of software, then a white box assessment may be the best option. If you are looking for a more comprehensive assessment of your overall security posture, then a grey box or black box assessment may be more appropriate.
Black Box Security Audit
 In the Black Box Security Audit, our team will only have access to publicly accessible information about the target environment. This type of test aims to simulate the real-world scenario of external attackers targeting and attempting to compromise your systems.
In the Black Box Security Audit, our team will only have access to publicly accessible information about the target environment. This type of test aims to simulate the real-world scenario of external attackers targeting and attempting to compromise your systems.
Black Box testing has the benefit of perfectly simulating a motivated external attacker that has zero-knowledge of your operations and IT infrastructure. It gives you an insight of the robustness of your information security controls when under targeted attack by malicious intruders.
White Box Security Audit
 In this approach our team would have as much information as possible about the target environment, such as an actual employee would possess. This approach is designed to prepare for a worst-case-scenario where an attacker has in-depth information about your infrastructure.
In this approach our team would have as much information as possible about the target environment, such as an actual employee would possess. This approach is designed to prepare for a worst-case-scenario where an attacker has in-depth information about your infrastructure.
White Box testing allows you to prepare for scenarios such as insider threats or an attacker that has obtained detailed internal information. This process usually reveals more vulnerabilities and is much faster since the audit team has transparent access to key information and details required for attacking the organization. Additionally, it extends the testing boundaries to areas such as source code audit, application design review etc. which are not usually covered by a traditional black-box audit.
Grey Box Security Audit
 In a Grey Box Security Audit our team would be given partial information about the target environment, such that could be identified by a motivated attacker. Documents provided could include policy documents, network diagrams and other valuable information. This approach aims to deliver a cost-effective audit while focusing on areas that are important to your organization.
In a Grey Box Security Audit our team would be given partial information about the target environment, such that could be identified by a motivated attacker. Documents provided could include policy documents, network diagrams and other valuable information. This approach aims to deliver a cost-effective audit while focusing on areas that are important to your organization.
Grey Box testing allows you to accurately simulate the threat from an attacker that has been able to gain partial information about your infrastructure. The audit prepares you for a scenario where certain details or information have been leaked by social engineering or other offline threats.